Educate your employees and customers about the dangers of phishing with this PowerPoint template in flat design.
Dangers of the Internet
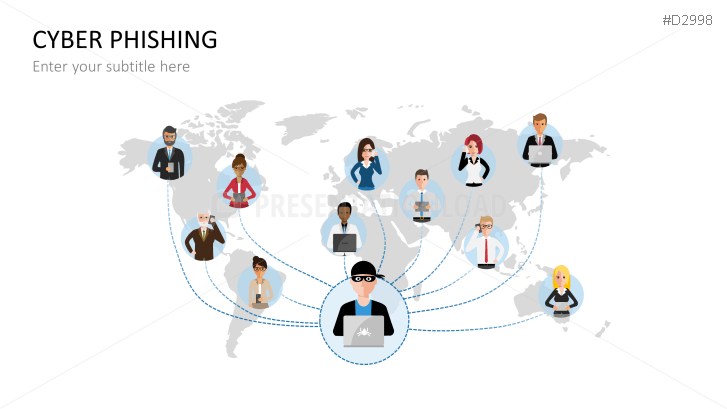
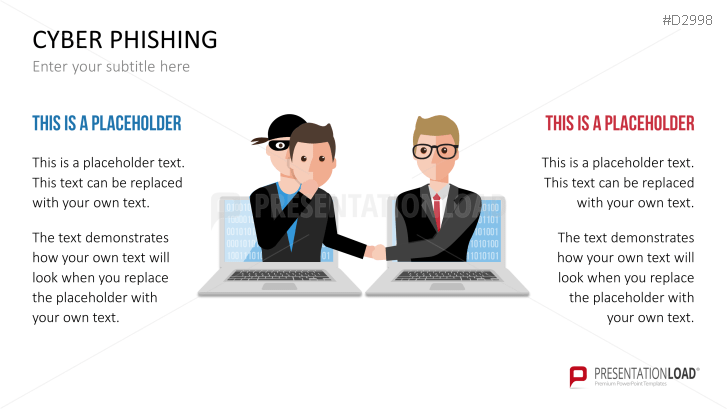
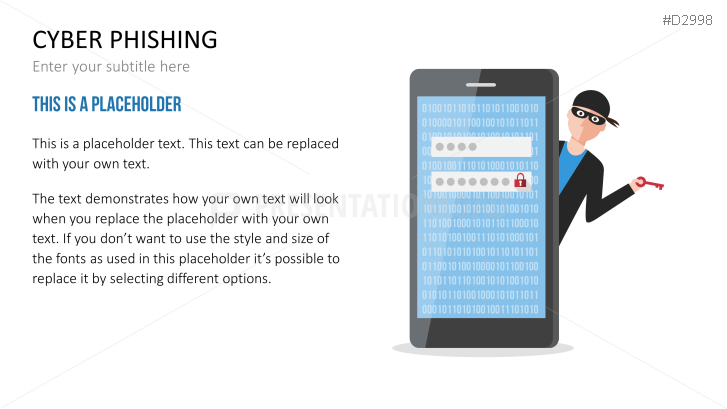
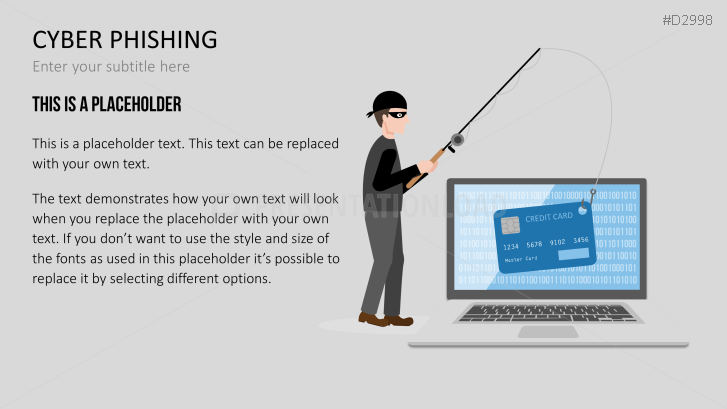
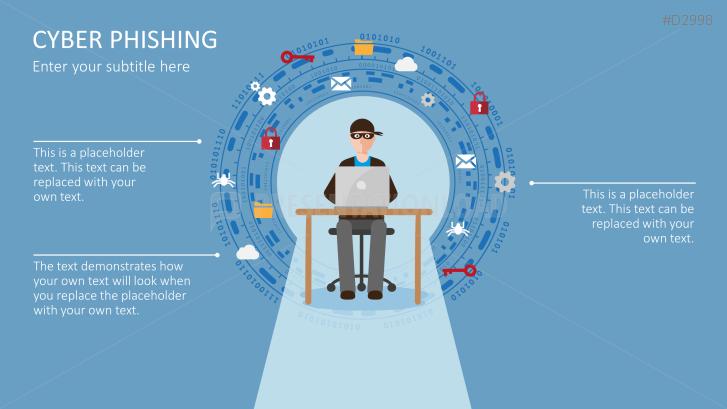
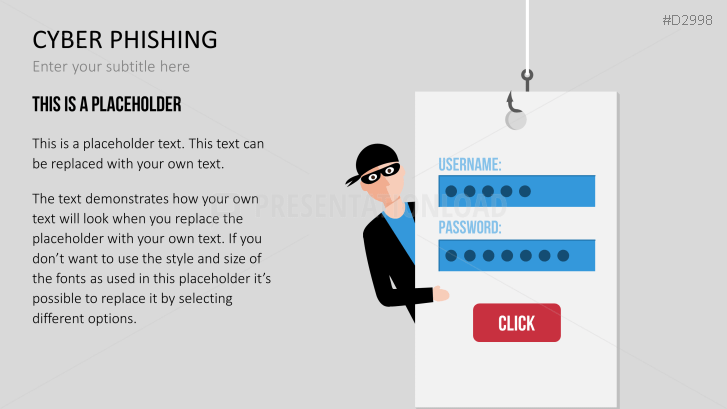
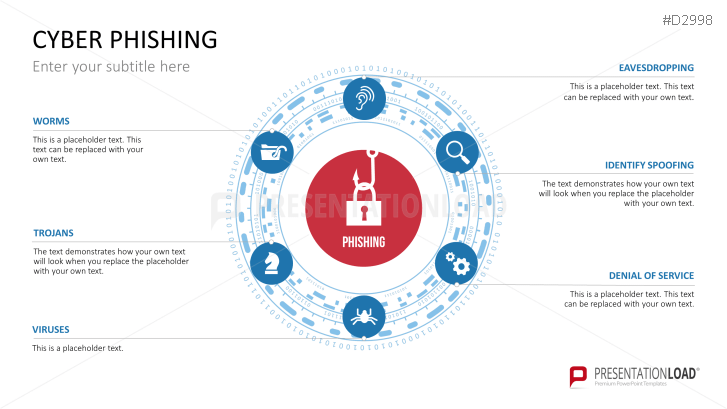
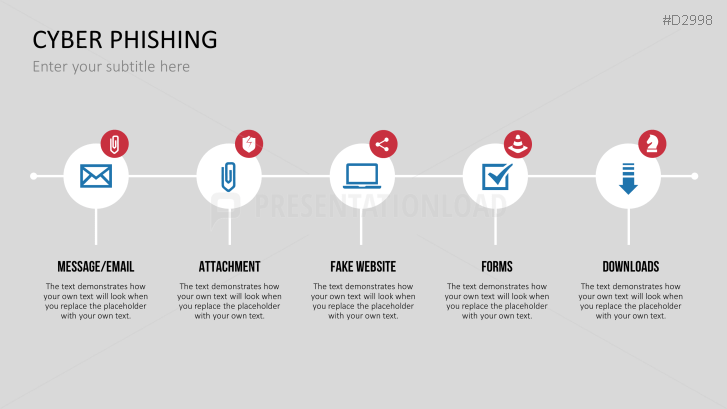
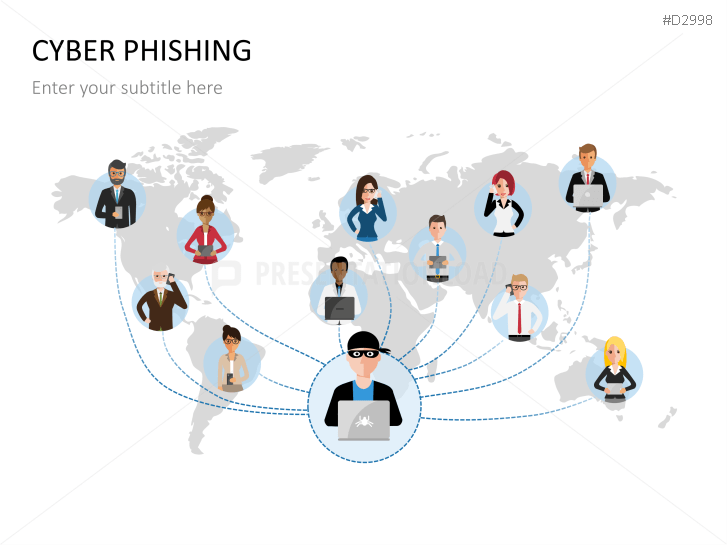
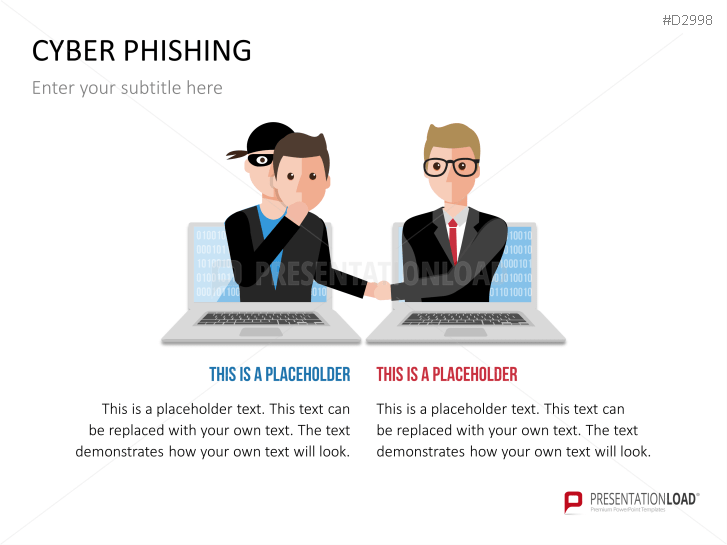
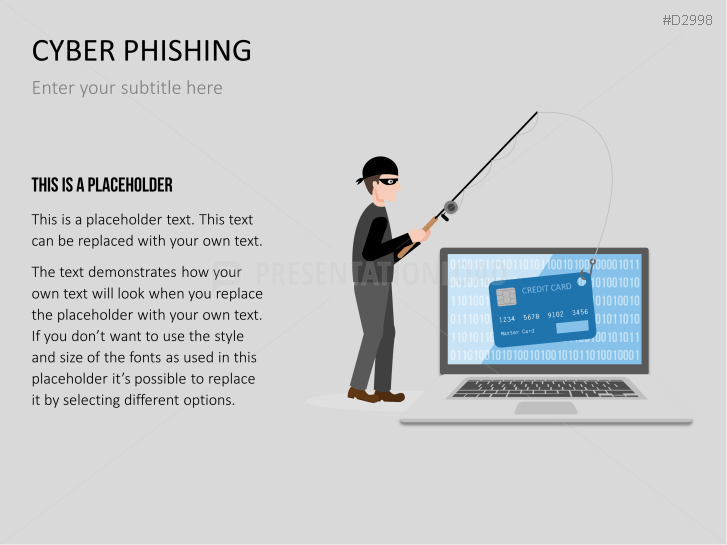
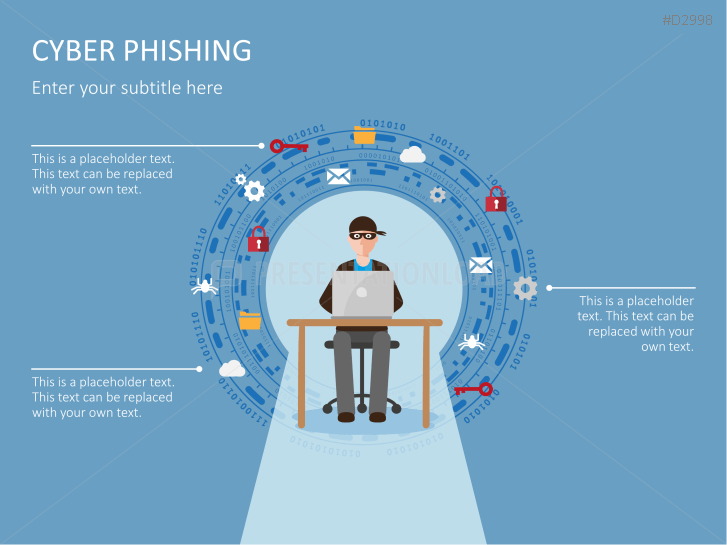
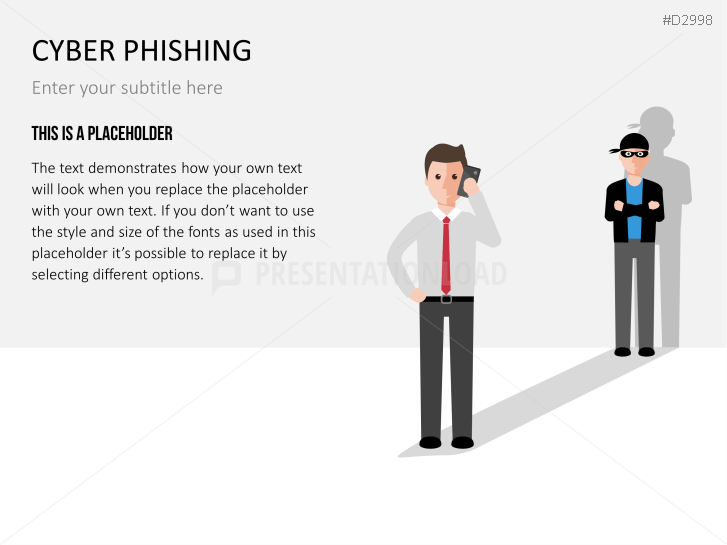
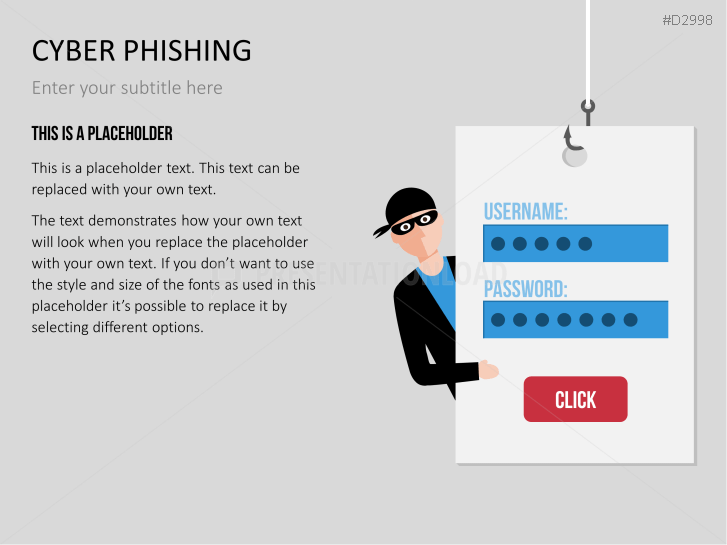
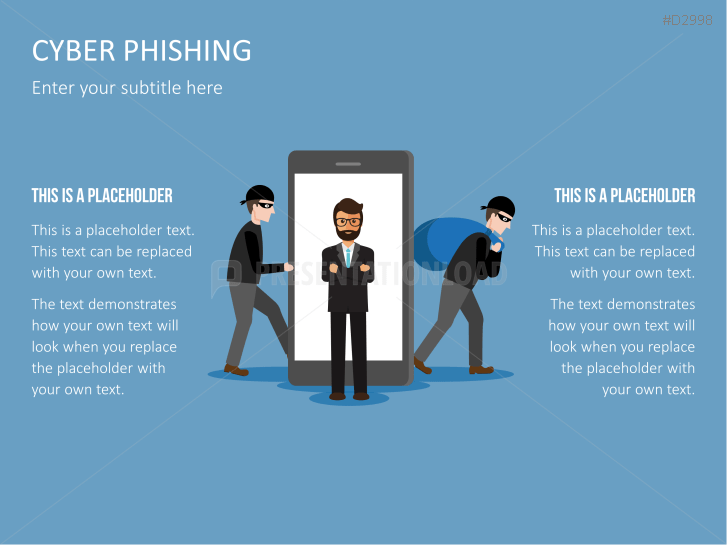
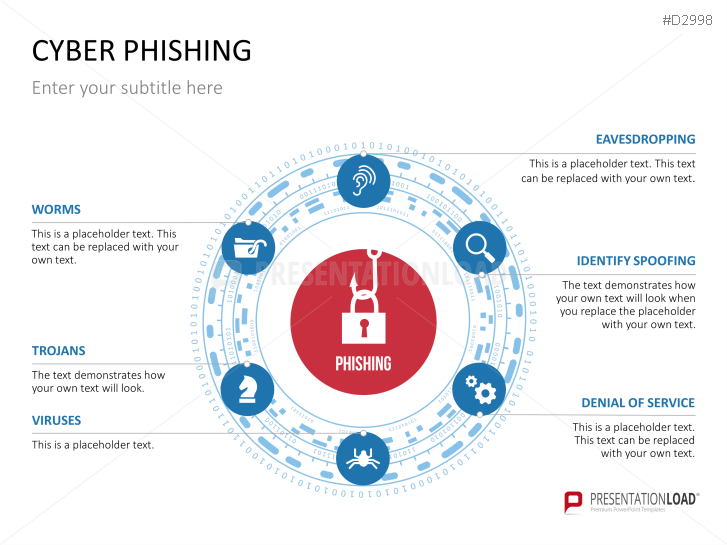
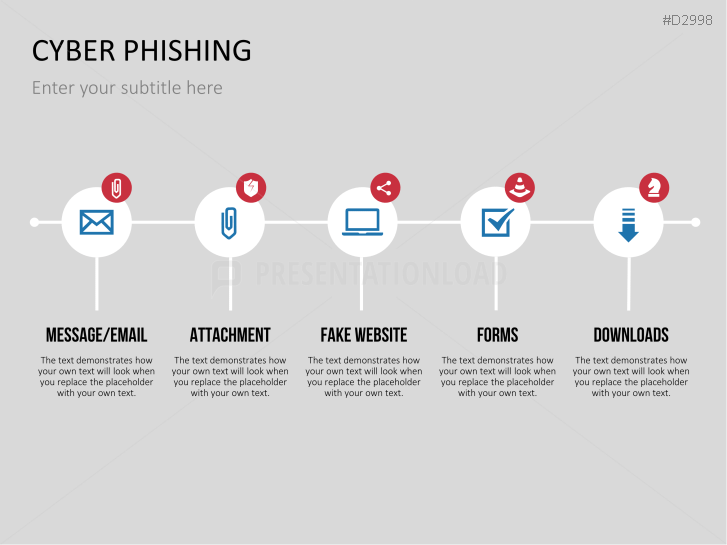
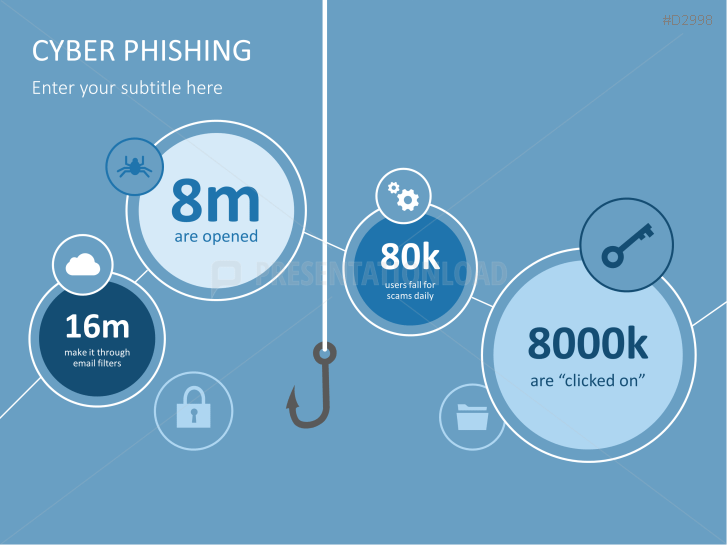
The term "phishing" is a homophone of the word fishing. Put into a digital context, phishing is the act of using "bait", such as fake websites, emails, or text, to obtain sensitive, personal information. For example, hackers can access the personal data of an Internet user, "fish" their password, and obtain credit card and account details. Victims often miss these traps because the websites and emails are imitations of trustworthy sites.
Visualize Phishing Methods and Protective Measures
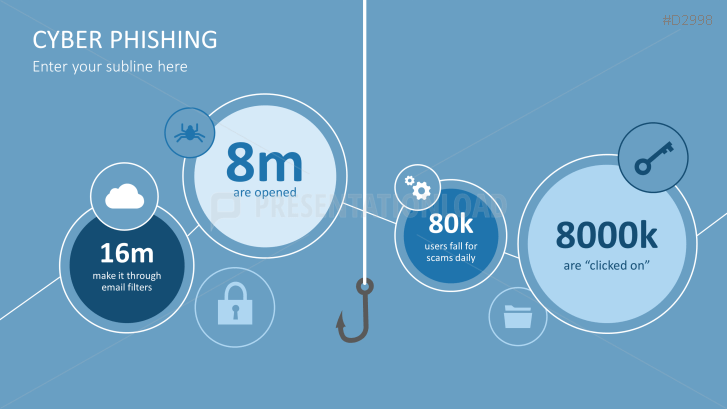
Phishing attacks are far too successful and prevalent. Internet users are not fully aware of what phishing methods are used or how to identify a fake email. Use our professionally designed PowerPoint template to inform your customers and employees about phishing and strengthen your defense against these hacker attacks.
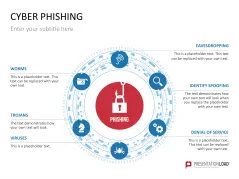
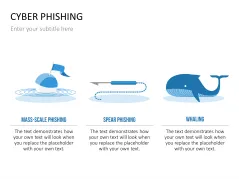
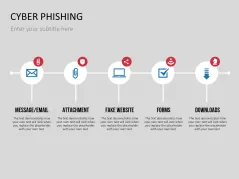
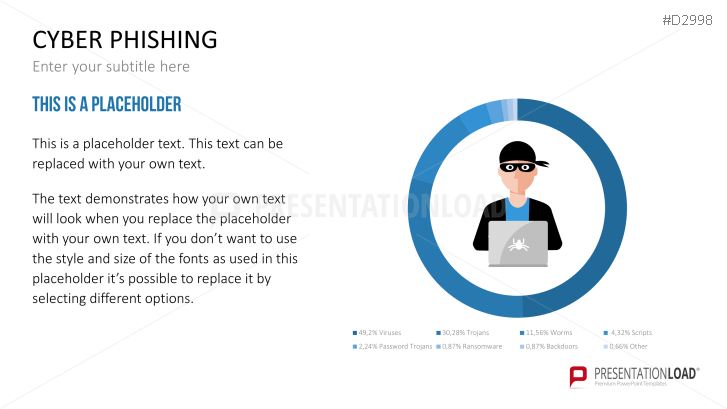
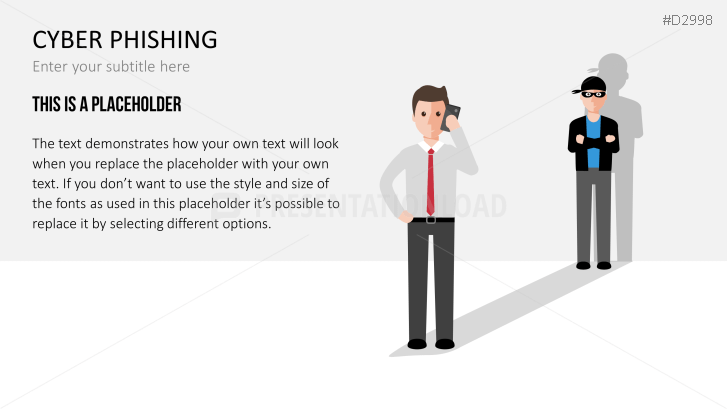
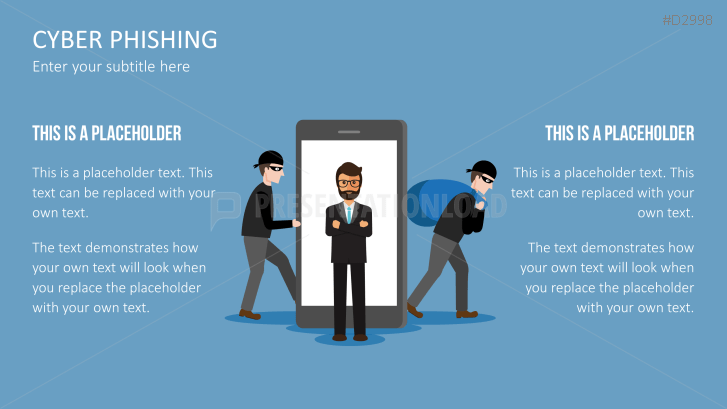
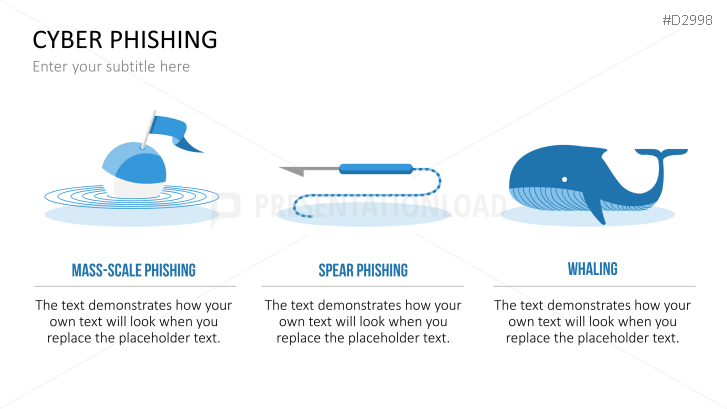
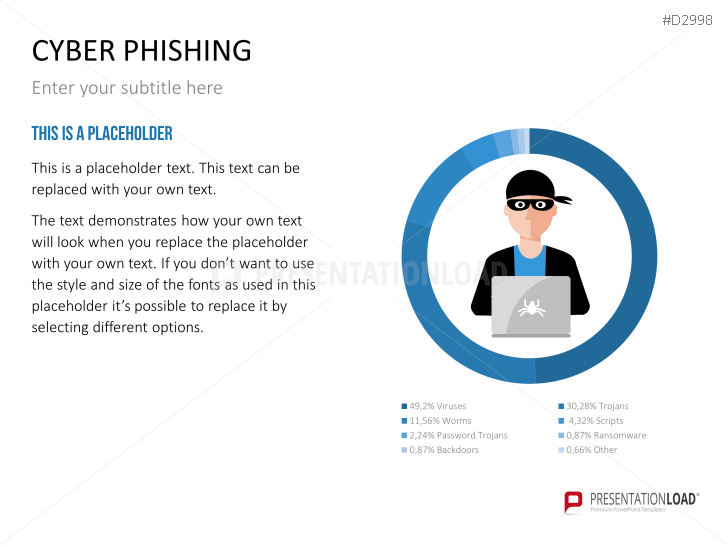
Fill the ready-made text placeholders with your own information on common Internet traps and take advantage of the numerous flat-design graphics and diagrams. Professionally designed graphics illustrate phishing with symbolic figures, such as a masked thief, fishing hooks, padlocks, password entry fields, credit cards, and much more.
With Our Cyber Phishing PowerPoint Template, You Can
- communicate the dangers of phishing
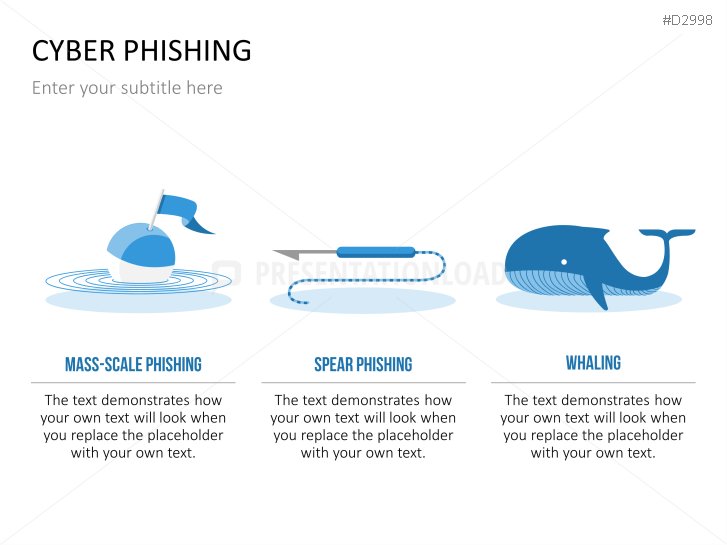
- explain different phishing methods
- illustrate warning signs and protective measures
This PowerPoint Template Includes:
- graphics and diagrams in flat design
- flat-design images of cyber criminals, phishing victims, etc.
- a collection of icons including laptop, email, and attachment
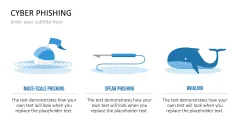
- a list of different phishing methods
- placeholders for your information